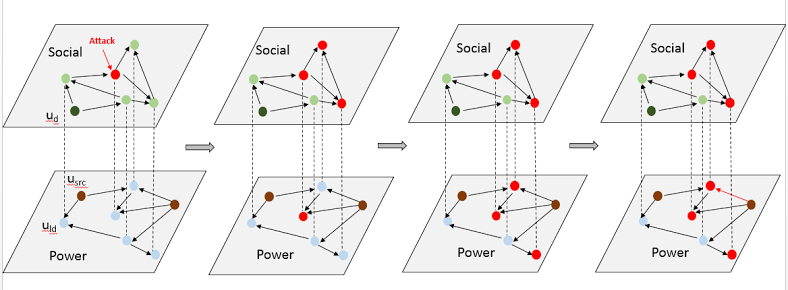
Vulnerabilities in Socially-Enabled Smart Grid
The social computing will integrate and enhance many digital systems over the next decade and the smart grid is no exception. Smart grid efficiency depends on utility customers having knowledge about demand response programs and being actively engaged in energy management. And this is exactly where social network comes into…... Read More
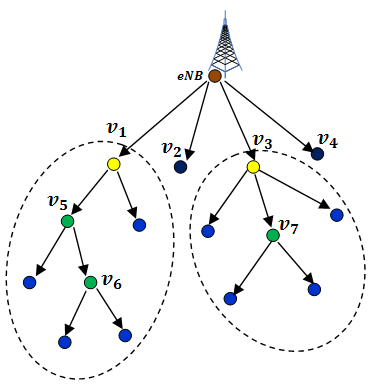
Spectral Efficiency and Resource Management
In cellular networks, rapid increase of data consumption has strained the network infrustructure. Proximity based device-to-device communication has been introduced as a way forward in next generation LTE networks. However, assigning limited resources efficiently to enable maximum reuse with spectral efficiency still remains an important challenge. As devices enter and…... Read More
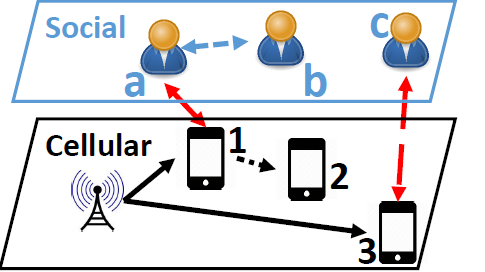
Socially Aware Schemes to Offload Network Traffic
Although Device-to-device (D2D) communications over licensed wireless spectrum has been recently proposed as a promising technology to meet the capacity crunch of next generation cellular networks, the success, to a large extent, depends on the willingness of the participating devices to share their resources. Consideration of social aspect of human…... Read More
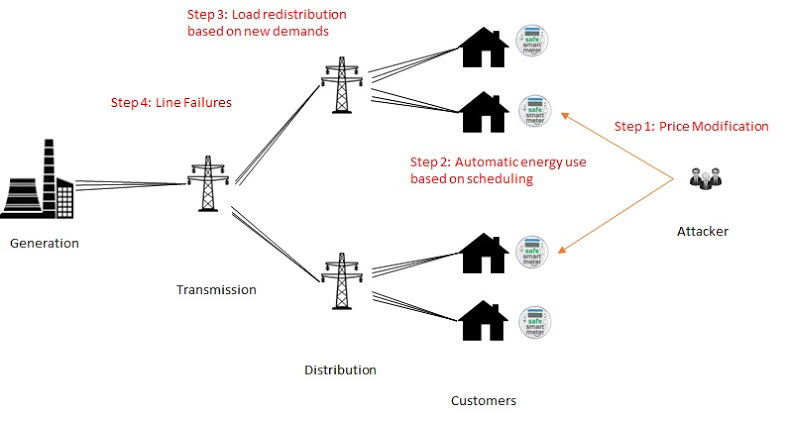
Price Modification and Load Distribution Attacks
Smart Grid addresses the problem of existing powergrid\'s increasing complexity, growing demand and requirement for greater reliability, through two-way communication and automated residential load control among others. These features also makes the Smart Grid a target for a number of cyber attacks. The load profiles of consumers could be changed…... Read More
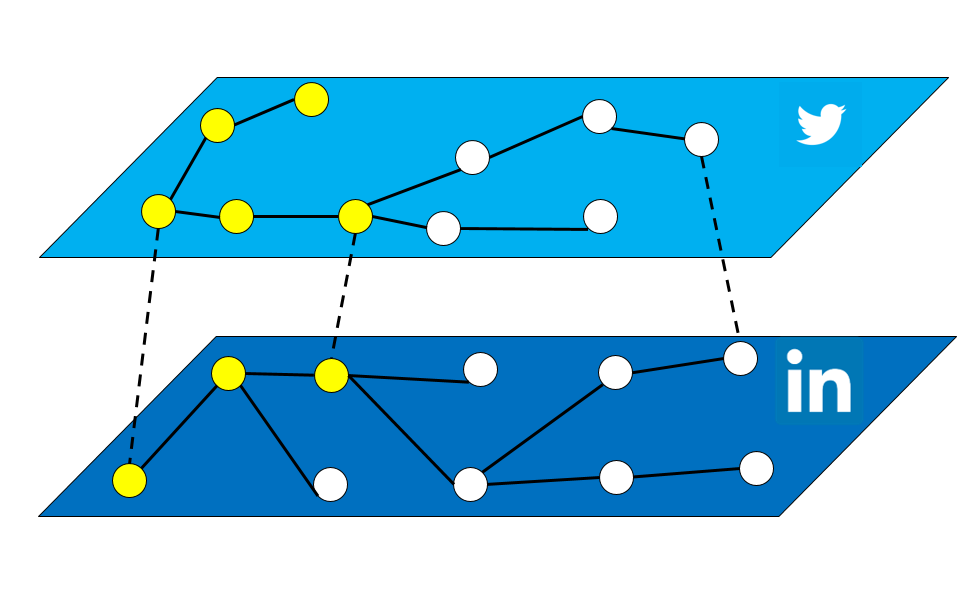
Modeling and Analysis of Multiplex Social Networks
Overlapping users of social networks such as Facebook and Twitter link these online social networks into a multiplex of social networks. As different components of the multiplex may have different properties, the multiplex may exhibit emergent phenomena that isn’t present in the simpler case of single layer social networks. For…... Read More
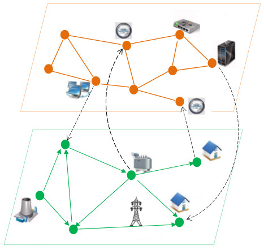
Vulnerability in Interdependent Networks
The study of interdependent networks from the perspective of vulnerability seeks to identify the critical elements with respect to a variety of measures. An interdependent system is robust if external perturbations do not significantly impair the functionality of the system. In this area, we seek to design methods to identify…... Read More
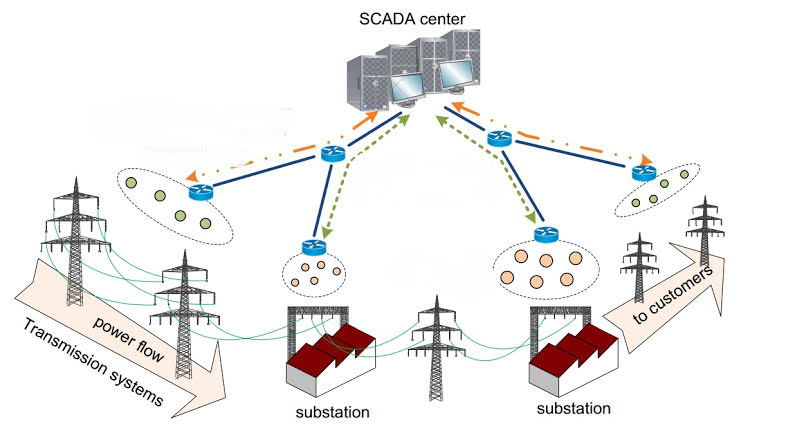
SCADA and DPI
Supervisory Control And Data Acquisition (SCADA) system remotely monitors and controls remote stations from a central SCADA center through coded signals over communication (or control) network. The addition of control network to better manage and gather system data comes with its own set of vulnerabilities including false data injection and…... Read More