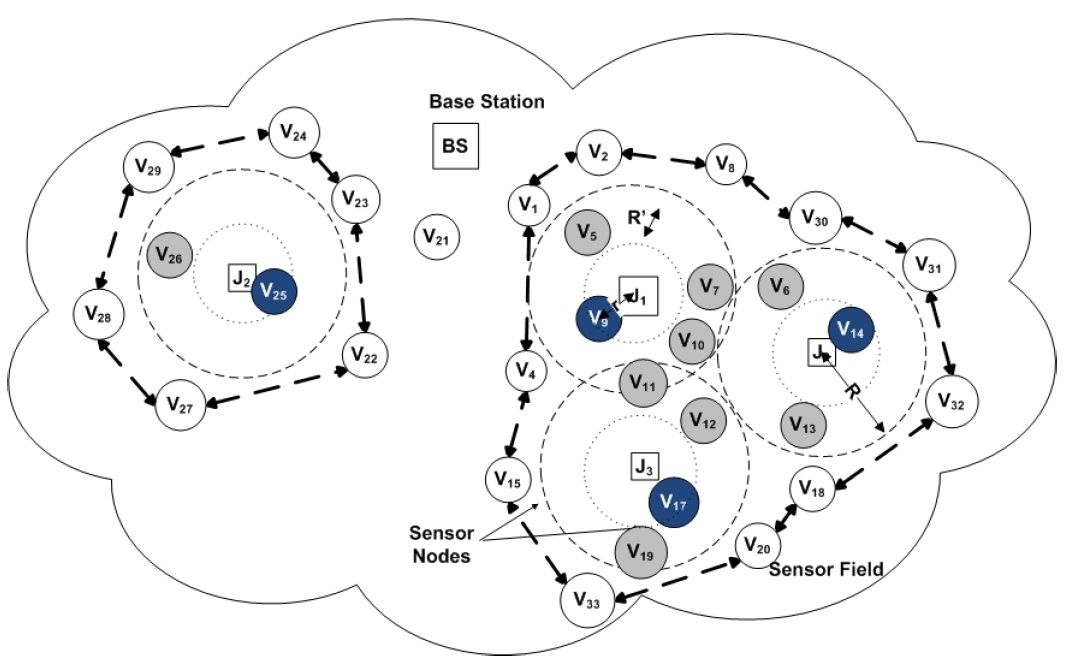
Group Testing and its Applications to Defending Denial-of-Service Attacks
Group Testing, also known as Pooling Design, is a technique to speed up the detection of affected blood samples within a large sample population in Biology. However, it has rarely been used for network security problems due to the limitations in its conventional models and algorithms. Investigating its advantage for…... Read More
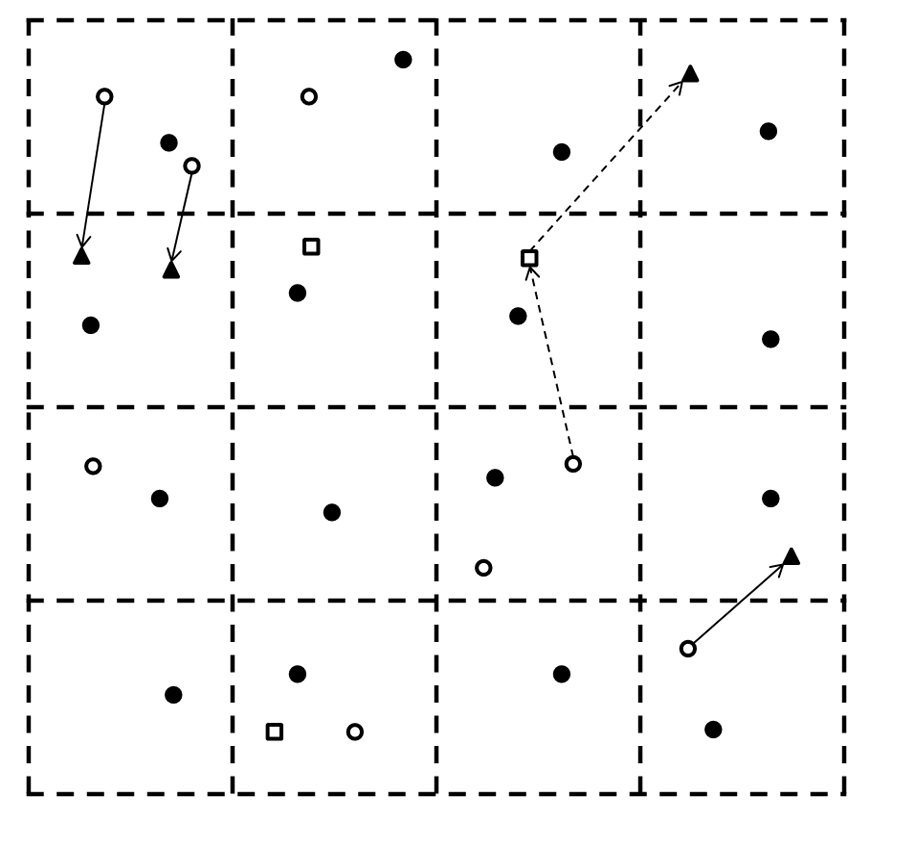
Wireless Network Coverage and Power Assignment
In wireless sensor networks, maintenance the network coverage is one of the most important tasks to guarantee the quality of monitoring results. There are many factors that affect the coverage of wireless sensor networks. In the deploying phase, the full coverage may not be achieved because of random deployment. Then…... Read More
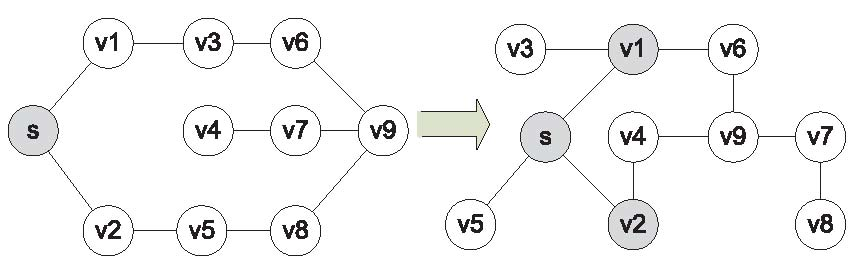
Broadcast Scheduling in Wireless Ad-Hoc Networks
Broadcast has been a fundamental mechanism to lower down delivery time latency in wireless ad hoc networks. The intrinsic broadcasting nature of radio communications can either speed up the communications by transmitting the message to all neighbors or slow down the communications because of the conflicts with other transmissions. Thus,…... Read More
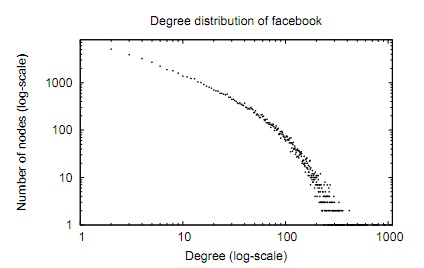
Vulnerability of Power Law Networks
In 1999, it is discovered that almost real large-scale networks follow the same type of graphs called power law graphs. In these realistic networks, the degree distribution follows the power law distribution, at least asymptotically. The fraction of nodes with degree k is proportional to the reciprocal of k power…... Read More