Privacy & Security in Learning Systems
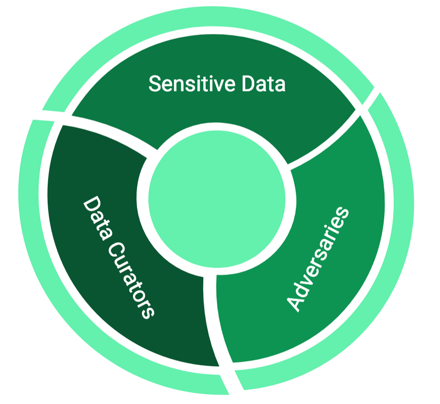
The ever-growing deployment of machine learning models in industrial and health contexts raises critical privacy and security concerns. These models are built on personal data (e.g. clinical records, images, and user profiles). Our work on this subject focuses on extending ideas in differential privacy to deep neural networks to secure…... Read More
Blockchain Security & Scalability
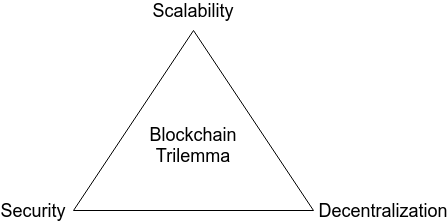
Although the blockchain technology has the potential to transform every industry, the performance level of existing blockchain platforms is too low to realize that vision. From an architectural viewpoint, this unsolved problem is a bottleneck to blockchain adoption in many applications. Our work aims to improve the scalability of blockchain to achieve Visa-like transaction…... Read More
Sybil attack and limiting the spread of misinformation
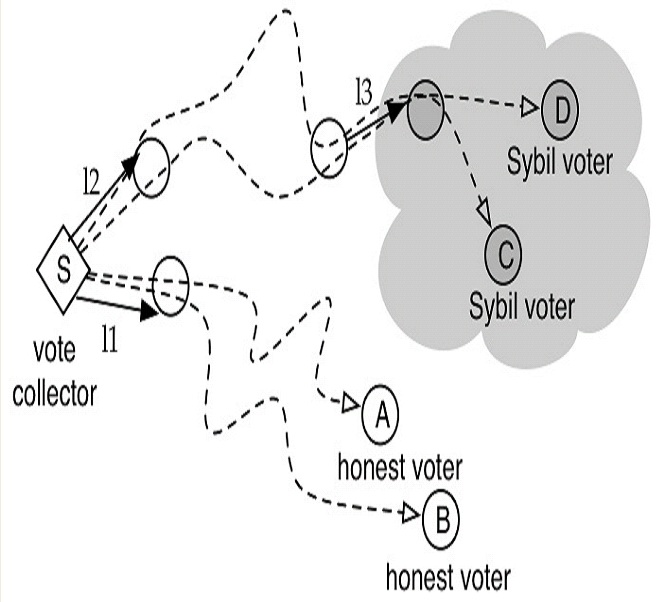
The wide spread of misinformation in online social networks has become a main threat to our society. Generally, people tend to believe what their friends are saying. Leveraging the social relationships to contain or block the misinformation appears to be a promising strategy. Objectives: Detect misinformation in online social networks…... Read More
Socialbot Behavior & Detection
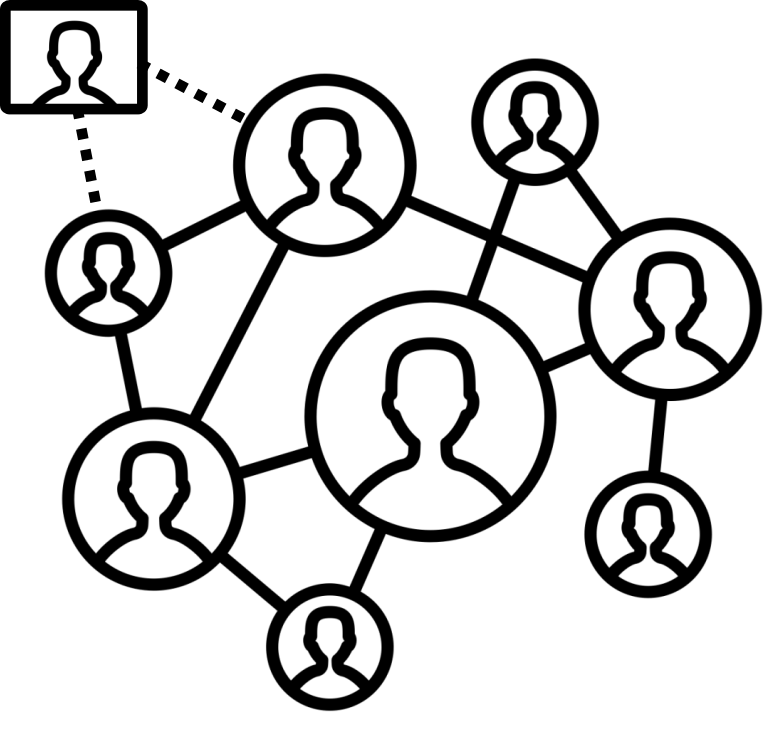
The socialbot attack model is a spiritual successor to the Sybil attack model that addresses several of its flaws. Where the Sybil model makes strong assumptions about the number and organization of the attackers, the socialbot model relaxes those. A socialbot is simply a bot that pretends to be a human on…... Read More
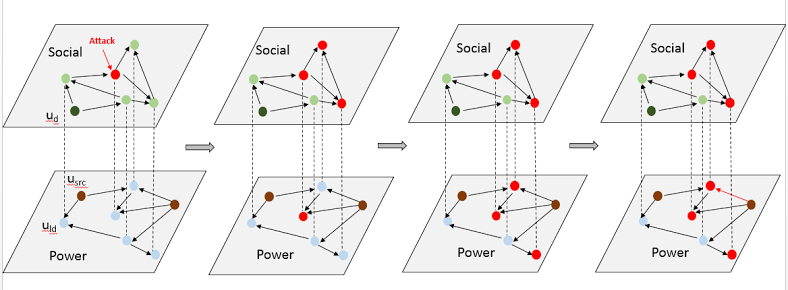
Vulnerabilities in Socially-Enabled Smart Grid
The social computing will integrate and enhance many digital systems over the next decade and the smart grid is no exception. Smart grid efficiency depends on utility customers having knowledge about demand response programs and being actively engaged in energy management. And this is exactly where social network comes into…... Read More
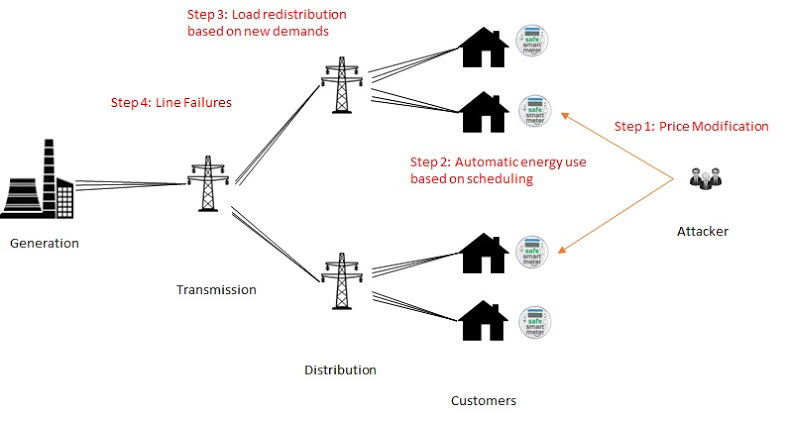
Price Modification and Load Distribution Attacks
Smart Grid addresses the problem of existing powergrid\'s increasing complexity, growing demand and requirement for greater reliability, through two-way communication and automated residential load control among others. These features also makes the Smart Grid a target for a number of cyber attacks. The load profiles of consumers could be changed…... Read More
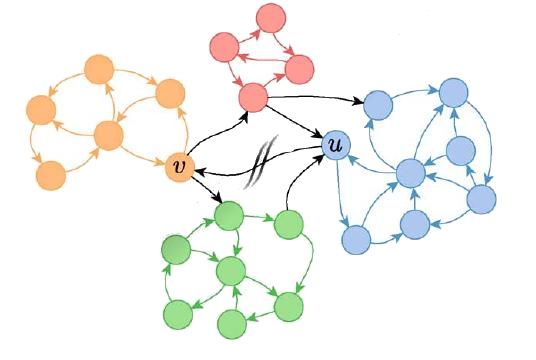
Complex Network Vulnerability Assessment
The study of network vulnerability seeks to identify the critical elements with respect to a variety of measures. Generally speaking, a network is robust if external pertubations do not significantly impair its functionality. In this area, we seek to design methods to identify the critical elements. One measure we study…... Read More
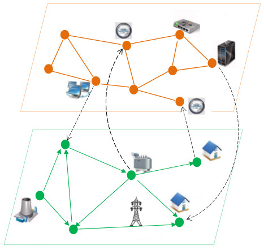
Vulnerability in Interdependent Networks
The study of interdependent networks from the perspective of vulnerability seeks to identify the critical elements with respect to a variety of measures. An interdependent system is robust if external perturbations do not significantly impair the functionality of the system. In this area, we seek to design methods to identify…... Read More
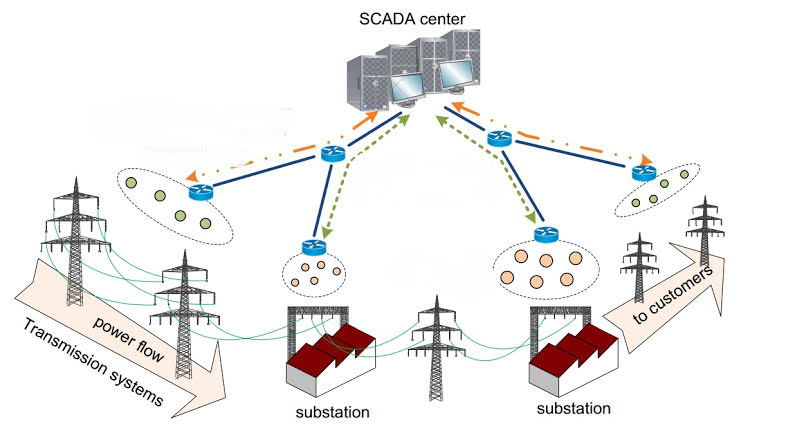
SCADA and DPI
Supervisory Control And Data Acquisition (SCADA) system remotely monitors and controls remote stations from a central SCADA center through coded signals over communication (or control) network. The addition of control network to better manage and gather system data comes with its own set of vulnerabilities including false data injection and…... Read More
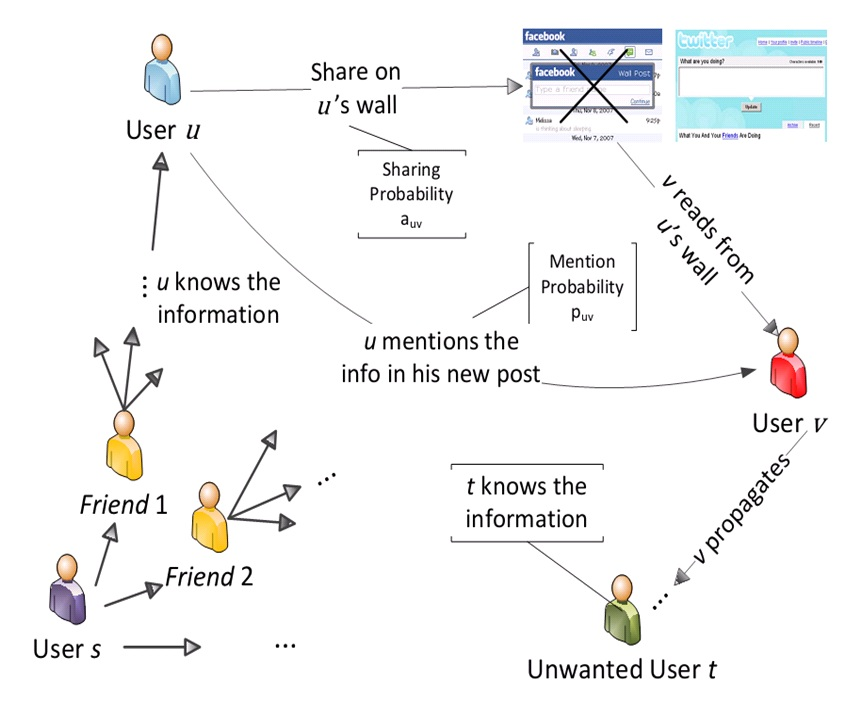
Information Leakage in Online Social Networks
As an imperative channel for rapid information propagation, OSNs also have their disruptive effects. One of them is the leakage of information, i.e., information could be spread via OSNs to the users whom we may not willing to share with. Thus the problem of constructing a circle of trust to…... Read More